LinkDaddy Cloud Services: Your Course to Seamless Data Administration
LinkDaddy Cloud Services: Your Course to Seamless Data Administration
Blog Article
Achieve Optimal Data Accessibility With Ingenious Cloud Storage Space Solutions
In the age of ever-expanding data volumes, the pursuit for attaining ideal data access has actually come to be a calculated crucial for contemporary enterprises. As businesses browse the complicated landscape of cloud storage solutions, the demand to effortlessly integrate cutting-edge techniques to improve information availability has arised as an important element of electronic improvement.
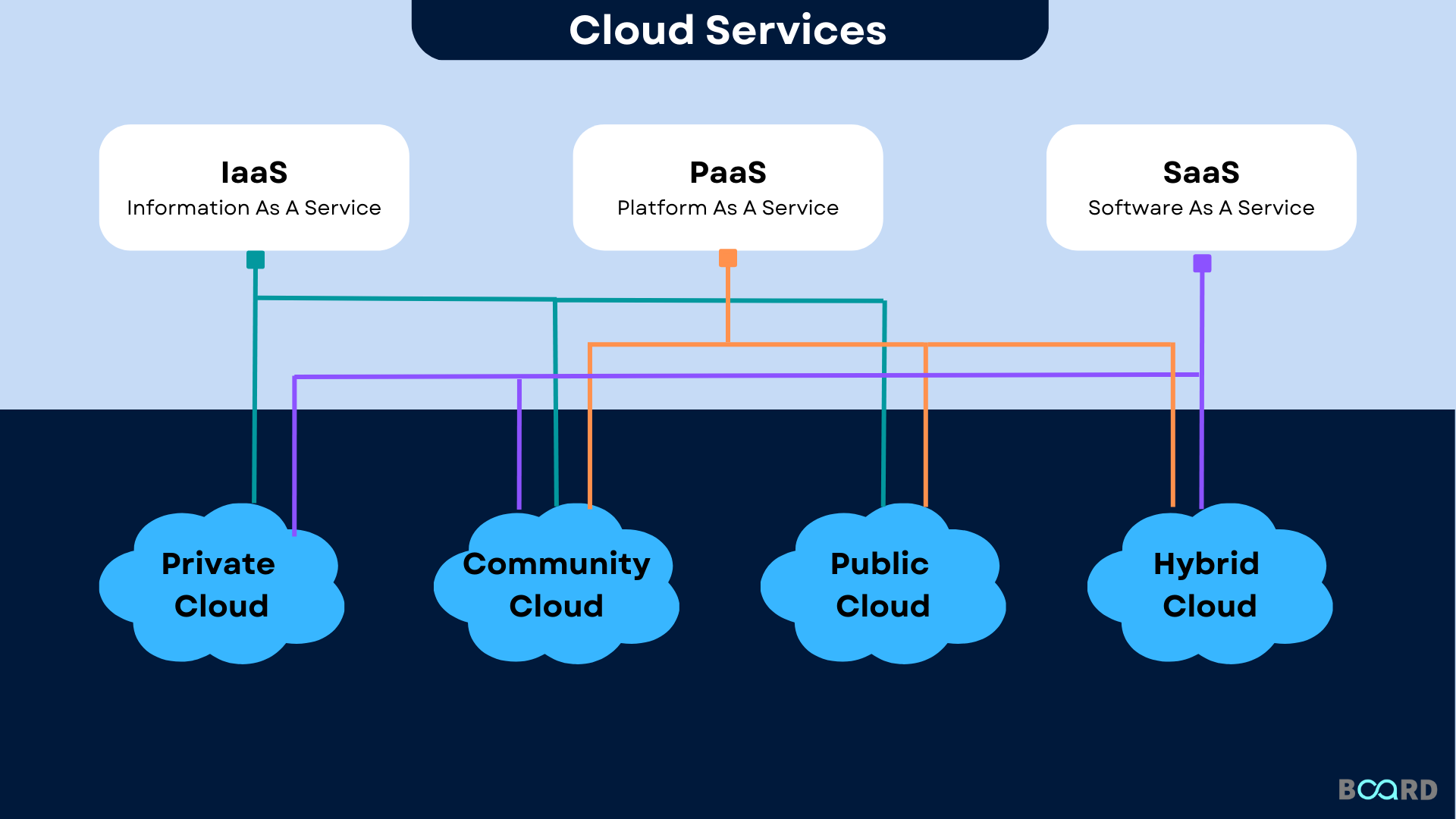
Benefits of Cloud Storage Space Solutions
Cloud storage space services supply a range of advantages that revolutionize data access and management in the digital age. Customers can securely access their data from anywhere with an internet connection, enabling remote job, cooperation, and smooth sharing of information.
Another considerable benefit of cloud storage space remedies is the scalability they offer. Services can quickly change their storage space needs based on demands, whether scaling up or down, without the demand for substantial ahead of time investment in equipment. This scalability makes sure that companies can adjust to changing information volumes and needs, eventually saving expenses and enhancing resource use.
In addition, cloud storage space remedies improve information protection by implementing durable security procedures and backup devices. This ensures that important info is protected against cyber dangers, data loss, and unauthorized gain access to.
Execution Techniques for Information Gain Access To
To enhance information accessibility performance and performance, companies need to purposefully prepare and implement robust strategies that straighten with their details information monitoring requires and objectives. One essential approach is to categorize information based upon its importance, regularity of access, and protection demands. By identifying data, companies can allocate and focus on resources storage options accordingly. Implementing information gain access to controls and authorizations is essential to ensure that just licensed people can access sensitive details. Making use of intelligent caching systems can likewise boost information access rates by keeping regularly accessed information better to the user.
Additionally, organizations need to take into consideration carrying out information compression and deduplication strategies to maximize storage room and boost data retrieval times. Using metadata tagging can better streamline data gain access to by supplying additional information about the content of documents. Regular tracking and performance tuning are crucial to identify bottlenecks and optimize data gain access to processes consistently. universal cloud Service. By utilizing these implementation methods, organizations can accomplish safe and secure and reliable information access tailored to their specific demands and needs.
Safety And Security Actions in Cloud Storage
Making sure robust safety steps is paramount when using cloud storage remedies for safeguarding sensitive information. Cloud storage space companies supply various protection functions to shield data from unauthorized gain access to, information violations, and various other cyber risks. Encryption plays a crucial role in protecting information stored in the cloud. By encrypting information both at rest and en route, companies can make sure that also if the information is intercepted, it remains unreadable to unauthorized events.
Furthermore, implementing access control steps is vital for maintaining information safety in cloud storage. Role-based accessibility control, multi-factor verification, and routine gain access to audits help in restricting access to sensitive details and stopping unauthorized users from getting entrance.
Enhancing Cooperation With Cloud Solutions
Collaborative process in contemporary companies are significantly streamlined through the integration of cloud services, promoting improved effectiveness and productivity amongst groups. Cloud solutions use a central platform where employee can access, modify, and share documents in real-time, getting rid of the requirement for back-and-forth e-mails or variation control issues. This real-time partnership function permits staff member to interact flawlessly, no matter of their physical location, resulting in quicker decision-making and job conclusion.
In addition, cloud remedies provide a protected atmosphere for partnership by using approvals and accessibility controls. Group leaders can assign specific access levels to individuals, ensuring that sensitive information is only available to authorized personnel. This enhances data security while promoting cooperation within the company.
In addition, cloud-based cooperation devices commonly come outfitted with communication features such as immediate messaging, video clip conferencing, and comment functionalities, promoting effective communication and idea sharing amongst staff member (linkdaddy cloud services). These devices aid in promoting a collective work society, driving technology and imagination within the organization
Scalability and Flexibility in Cloud Storage Space
Attaining ideal scalability and versatility in cloud storage space systems is imperative for suiting dynamic data needs in contemporary enterprises. Scalability describes the system's capability to handle expanding amounts of information and individual demands successfully. Cloud storage remedies use scalability by allowing companies to quickly increase or reduce storage ability based on their demands, getting rid of the constraints of standard on-premises storage space facilities. Versatility in cloud storage space relate to the versatility in accessing, managing, and saving data throughout different platforms and tools. Modern cloud storage options provide companies with the adaptability to integrate with numerous applications, enable remote access to information, and support collective workplace. This versatility boosts productivity and enhances workflows by guaranteeing smooth information access and sharing. By leveraging adaptable and scalable cloud storage services, ventures can adjust to changing company needs, maximize resource usage, and preserve my explanation an affordable side in today's data-driven landscape.

Conclusion
To conclude, accepting cutting-edge cloud storage space remedies offers numerous benefits for companies, including effective data categorization, robust gain access to controls, advanced caching methods, and streamlined gain access to image source with metadata tagging. By carrying out these methods, organizations can improve partnership, reinforce safety procedures, and make sure ideal data retrieval. The scalability and flexibility of cloud storage solutions further encourage groups to function perfectly and make informed decisions, inevitably driving organization success in today's electronic landscape.
In the age of ever-expanding data quantities, the pursuit for accomplishing ideal data accessibility has actually ended up being a strategic essential for modern ventures.To improve data accessibility effectiveness and efficiency, companies have to tactically plan and apply robust techniques that straighten with their certain data monitoring needs and objectives. Making use of intelligent caching devices can likewise enhance information access rates by storing regularly accessed data more detailed to the individual.
Moreover, companies ought to take into consideration executing information compression and deduplication methods to maximize storage area and boost data access times (cloud services press release). Cloud storage suppliers offer different security functions to protect data from unauthorized accessibility, data breaches, and various other cyber threats
Report this page